Project information
- Category: Project
- Project date: November, 2022
- Project Report: Latis Report
Latis
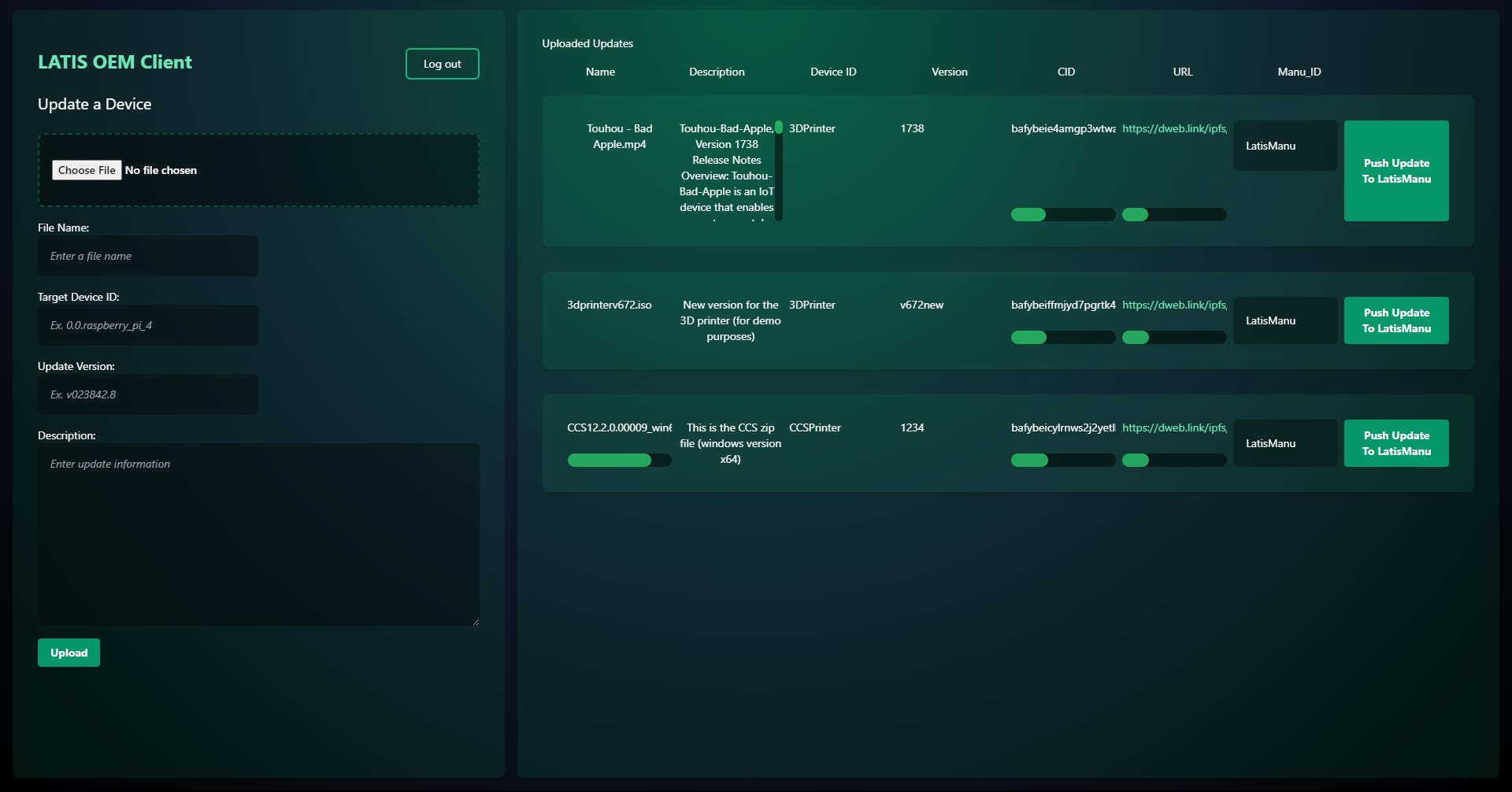
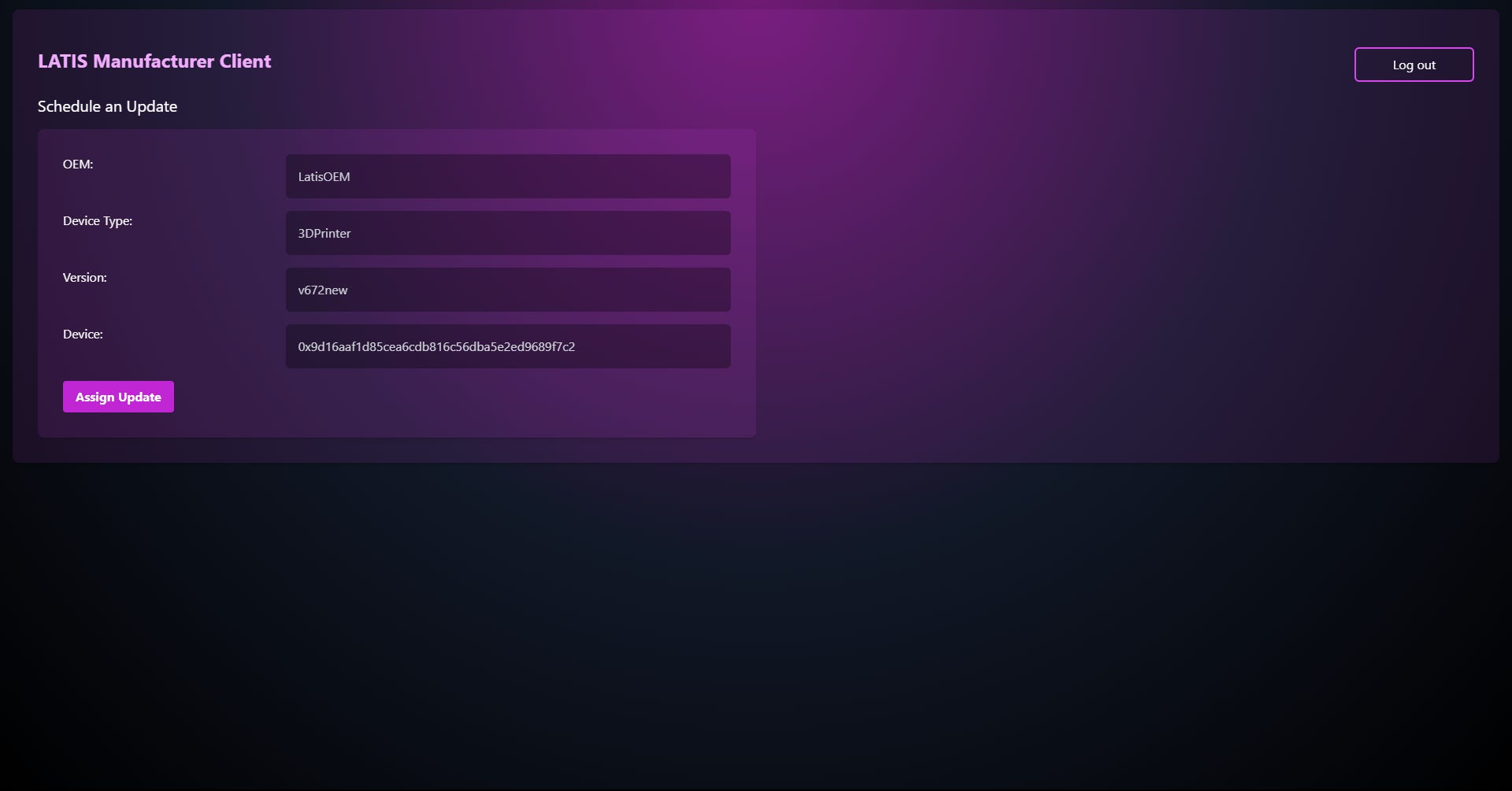
Worked with industry experts to understand the issues involved with updating IoT devices in manufacturing plants. Created a system that allows for the easy updating of Scada systems in manufacturing plants using Hedera's Hashgraph and Filecoin's IPFS to store the data. The system allows for easy transfer of updates from the OEM (equipment maker) to the manufacturing plant, and allows for direct communication to the device without any manipulation by the manufacturing plant reducing the risk of cyberattacks.
Problem
Currently, there are over 27 billion IoT devices in use, and this number is projected to increase in the future. These devices are utilized across various industries, including manufacturing, healthcare, and transportation. However, recent research conducted by the World Economic Forum has identified manufacturing as the most targeted sector, and with the growing number of IoT devices, the risk of cyberattacks is also on the rise.
Solution
To address this issue, we have developed a decentralized system that facilitates the seamless updating of IoT systems in the manufacturing sector. Our approach establishes inherent trust in the system by utilizing Hedera's Hashgraph to securely store sensitive information like encryption keys. Additionally, Filecoin's IPFS is employed to store update files. This system enables easy transfer of updates from the equipment manufacturer to the manufacturing plant while ensuring direct device communication without any interference from the plant, thereby reducing the risk of cyberattacks.
Business Plan
When presenting this concept to industry experts, we have positioned it as a hardware as a service (HaaS) model. Manufacturers can choose to adopt this system by paying an annual flat fee and entering into a minimum 3-year service contract. The original equipment manufacturer (OEM) will have a predetermined limit on the number of updates per quarter and will be charged a flat rate for using the system. The rationale behind this approach is that if our system can prevent even a single cyberattack, it will prove cost-effective for decades to come, considering the substantial financial losses typically associated with such attacks.